Everything You Need to Know About Device Usage Policy
Proper device management safeguards company data and ensures productivity. A straightforward Device Usage Policy sets clear guidelines for secure, responsible use, reducing risks and simplifying compliance for HR and IT teams.
What is a Device Usage Policy?
A Device Usage Policy is an IT and HR guideline that sets expectations for the use of company-owned and personal devices in the workplace. It covers acceptable use of technology, data security protocols, and compliance with cybersecurity standards like GDPR or HIPAA, depending on the industry.
The policy addresses issues such as internet usage, software installations, data confidentiality, and the handling of sensitive information, ensuring that employees use devices responsibly without compromising organizational security. A well-defined device usage policy helps prevent data breaches, protect intellectual property, and maintain operational efficiency.
Guidelines for Creating a Device Usage Policy
A well-crafted Device Usage Policy helps secure company data and ensures responsible technology use. Follow these steps:
State the Purpose and Scope of Device Use
Clarify that the policy applies to all company-owned devices, as well as personal devices that may be used for work purposes (BYOD), to protect both company resources and sensitive information.
Define Acceptable and Unacceptable Use
Outline the acceptable uses of devices, including work-related tasks and communications, while specifying prohibitions such as personal use during work hours, illegal activities, and downloading unauthorized software.
Include Security Measures
Provide guidelines for securing devices, including password policies, encryption requirements, and VPN usage. Ensure employees understand their role in protecting company data from cyber threats and data breaches.
Establish Internet and Social Media Guidelines
Set clear boundaries for internet browsing, social media activity, and external communications, particularly in regard to maintaining professionalism and protecting company reputation.
Detail Mobile Device Management (MDM) Protocols
If applicable, specify MDM protocols for tracking, managing, and remotely wiping company devices in case of loss, theft, or termination of employment to prevent data breaches.
Clarify Remote Work and Bring Your Own Device (BYOD) Rules
Provide specific guidelines for remote workers using personal devices, including security protocols, company-owned software, and data protection measures that need to be followed.
What is Covered in a Device Usage Policy?
An effective device usage policy should include the following:
Acceptable Use of Devices
Explanation of what constitutes appropriate use of company devices, including work-related tasks, communication, and internet usage, as well as prohibitions on personal use during work hours.
Security Protocols
Guidelines for securing company devices, including password requirements, encryption, VPN usage, and regular security updates to protect company data.
Mobile Device Management (MDM)
Instructions on the management of mobile devices, including tracking, remote wiping, and security measures to protect sensitive company information.
Data Protection and Privacy
How employees should protect company data on devices, including the use of secure networks and handling of confidential information.
Remote Work and BYOD (Bring Your Own Device)
Guidelines for employees working remotely or using personal devices for work, ensuring they follow the same security protocols as company-issued devices.
Disciplinary Actions for Misuse
Clear consequences for violating the device usage policy, such as restricting access, disciplinary actions, or termination in cases of misuse.
Monitoring and Access
Explanation of any monitoring tools the organization may use to ensure devices are being used according to policy, including monitoring of internet traffic and device location.
Legal Compliance
Reference to data protection laws such as GDPR, HIPAA, or PCI-DSS (if applicable), and how the policy aligns with these regulations.
Need help creating a device usage policy?
How Winslow Helps HR Teams Streamline Device Usage Policy
Clear device usage policies help protect company data and ensure compliance. Winslow makes managing these policies easier by:
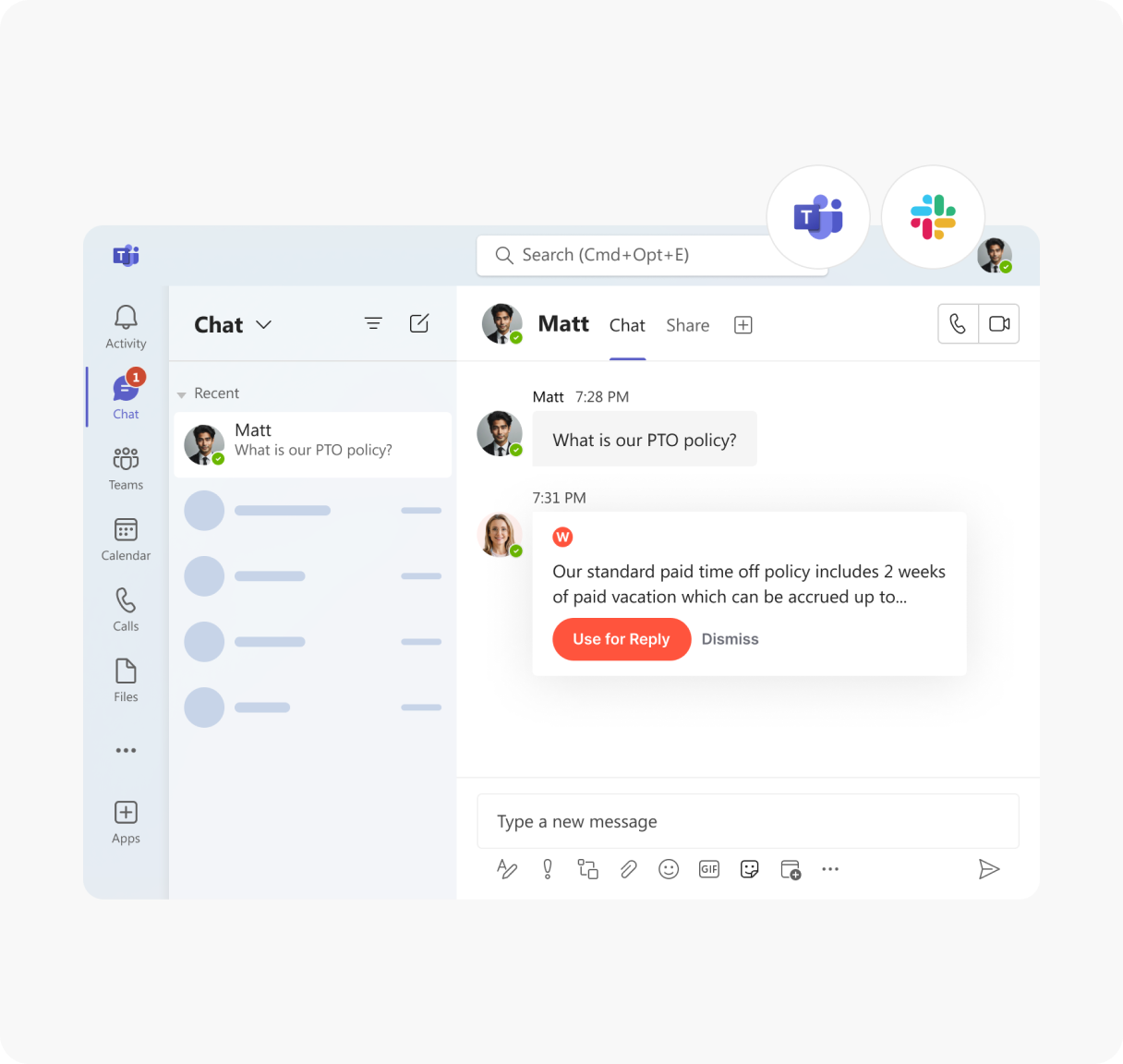
Instant answers anytime
Winslow provides on-demand access to your Device Usage Policy via Slack, Teams, or email. Employees can instantly check guidelines on personal vs. company device use, security protocols, and acceptable usage—reducing risks and ensuring compliance with IT policies.
Personalized Support
Winslow instantly answers HR questions, including those about our Device Usage Policy, ensuring clarity on company guidelines and security practices.
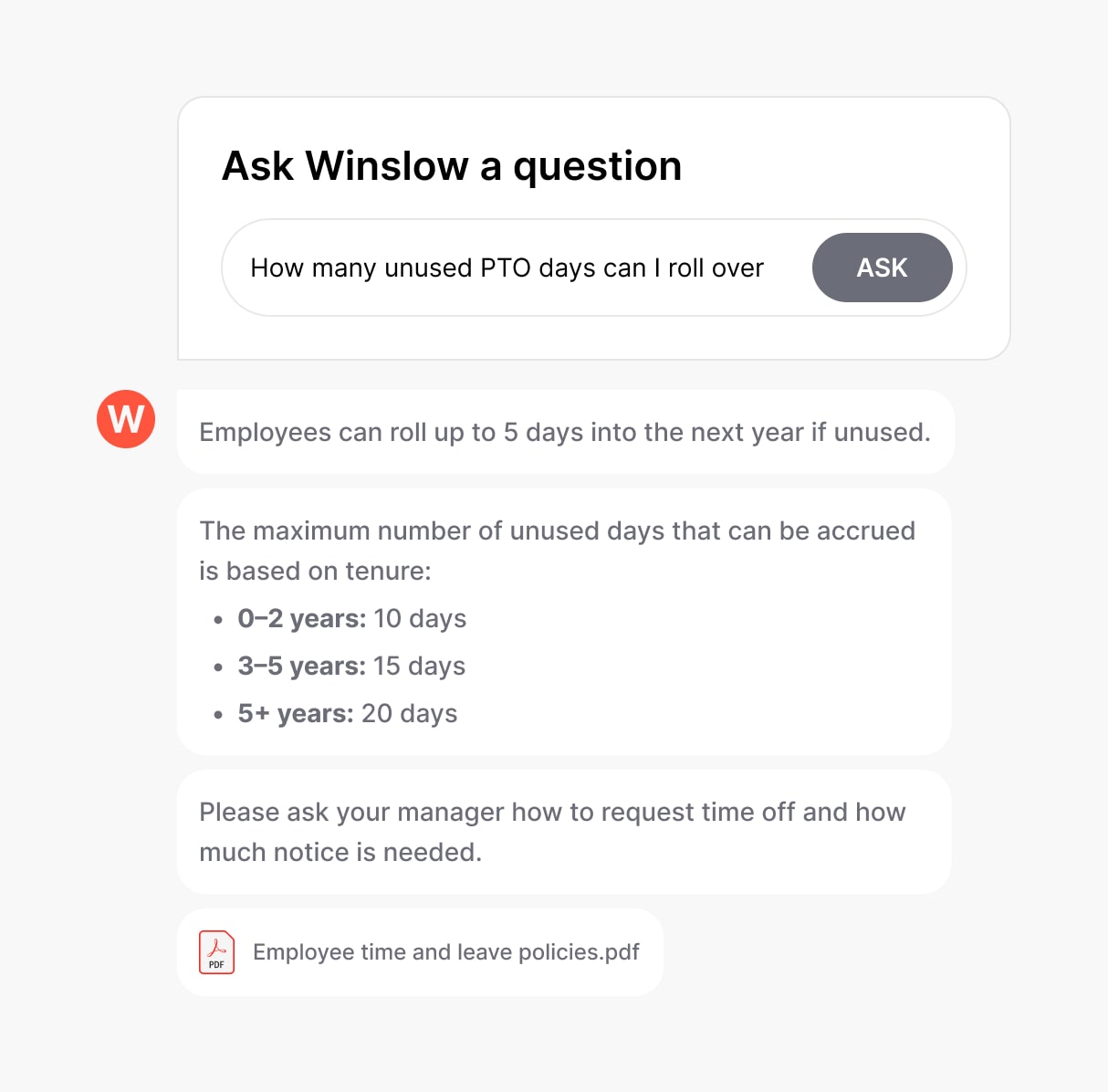
Analytics and Insights
Winslow tracks policy-related queries, helping HR teams identify trends and common concerns. This data enables organizations to refine their policy, improve reporting channels, and address recurring issues proactively.
Streamline Device Usage Policy Management with Winslow
With Winslow, HR can effortlessly manage and address device usage policy inquiries, helping employees stay compliant and protecting company data with clear and consistent guidelines.
Frequently asked questions
Have further questions about Winslow, contact us at sales@usewinslow.com
How can HR balance employee privacy with the need for monitoring device usage?
HR can balance privacy and monitoring by clearly defining the scope of monitoring in the device usage policy, informing employees about the extent of monitoring, and ensuring that monitoring is limited to business-related activities. Consent should be obtained where necessary, and privacy must be respected within legal boundaries.
What steps should HR take when an employee violates the device usage policy?
HR should first investigate the violation, ensure the employee understands the rules, and issue a warning or take corrective action as appropriate. Repeated violations may lead to disciplinary measures, including suspension or termination, depending on the severity of the breach.
How can HR educate employees about the importance of adhering to the device usage policy?
HR should communicate the policy during onboarding and conduct regular training on cybersecurity and data protection. Reminders should be issued periodically to ensure employees understand the risks of improper device use and the importance of protecting company data.
What are the legal implications of monitoring employee device usage?
Monitoring employee device usage may raise privacy concerns. HR must comply with local, state, and federal laws, including the Electronic Communications Privacy Act (ECPA) and any state-specific privacy laws. It’s important to inform employees of monitoring practices and ensure transparency in compliance with legal requirements.
Additional resources
confidentiality policy
Protecting sensitive information is crucial. A clear Confidentiality Policy outlines guidelines for...
Learn moreclaim reimbursement
Ensuring fair compensation for expenses is key. A clear Claim Reimbursement Policy...
Learn morepayment policy
Ensuring timely and fair compensation is essential. A clear Payment Policy outlines...
Learn more




